Want to build your AI module or
an entire AI platform?
2 implementation models
Want to build your AI module or
an entire AI platform?
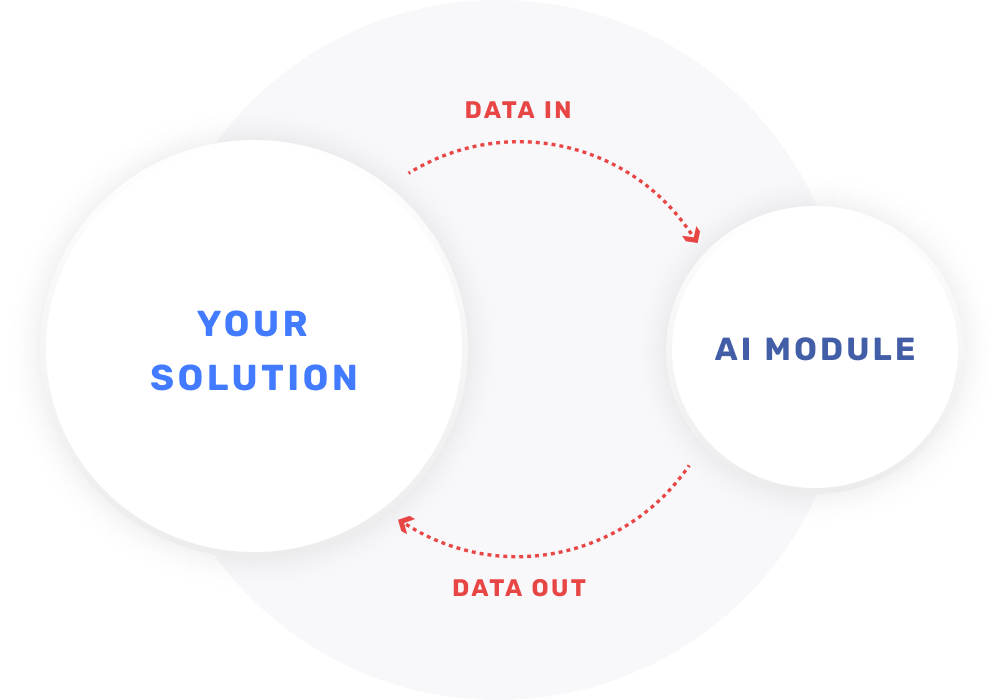
AI Module
Integrate AI seamlessly into your existing systems to enhance functionalities, whether it’s for SaaS applications, internal systems, or dedicated software.

AI Platform
Develop a custom, stand-alone AI solution tailored to your needs, whether for internal use or as a marketable product.
Download a report!
How do AI Custom Solutions work?
The best way to explain this is through real-world examples. When you watch movies on Netix or listen to music on Spotify, both platforms collect your behavioral data, process it using AI (pattern recognition and predictive analysis), and then offer you recommendations through their recommendation engines.
Data Collection
Data Processing
(the AI core system)
Results
AI use cases
Practical applications of AI to enhance your business operations
Predictive Analytics
Recommendation
Engine
Natural Language
Processing (NLP)
Image & video Recognition
Pattern & Anomaly
Detection
Content Generation
Research
Automation
Scoring Models
Case study
AI Platform for risk decision engine
We created a SaaS platform from scratch that enables loan and credit businesses to make quicker and smarter decisions. This was achieved using a decision-facilitating and scoring engine based on AI and ML mechanisms.
Result:
- 80% cost reduction on new features
- 80% maintenance costs reduction;
- 50% infrastructure cost reduction
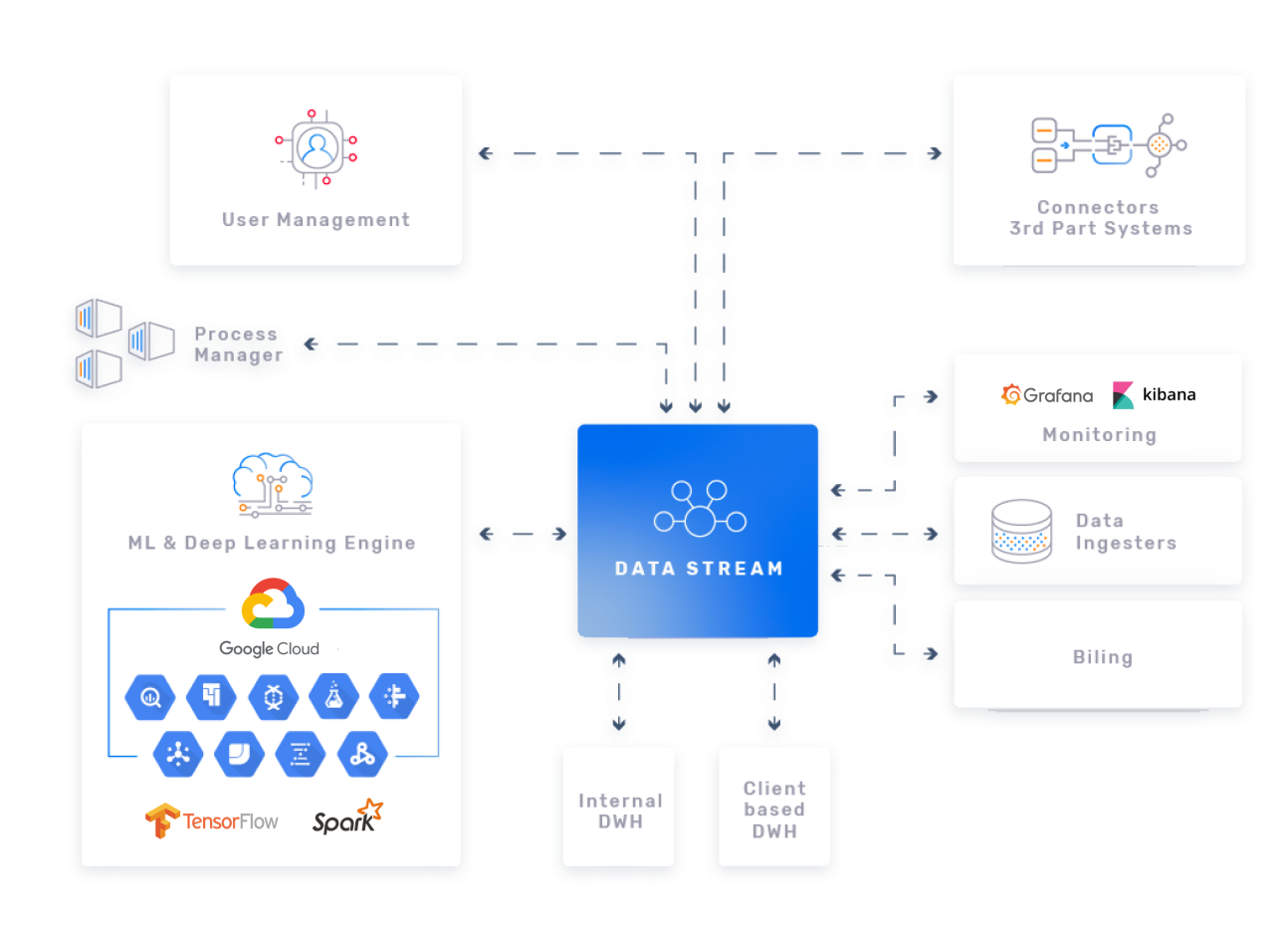
How does it work?
Once we have the Discovery & Exploration phase behind us, we proceed with AI Development. Step by step, we prepare the infrastructure and frameworks to iteratively enhance your business. We invite you into the real battlefield, where you will gain a competitive advantage.
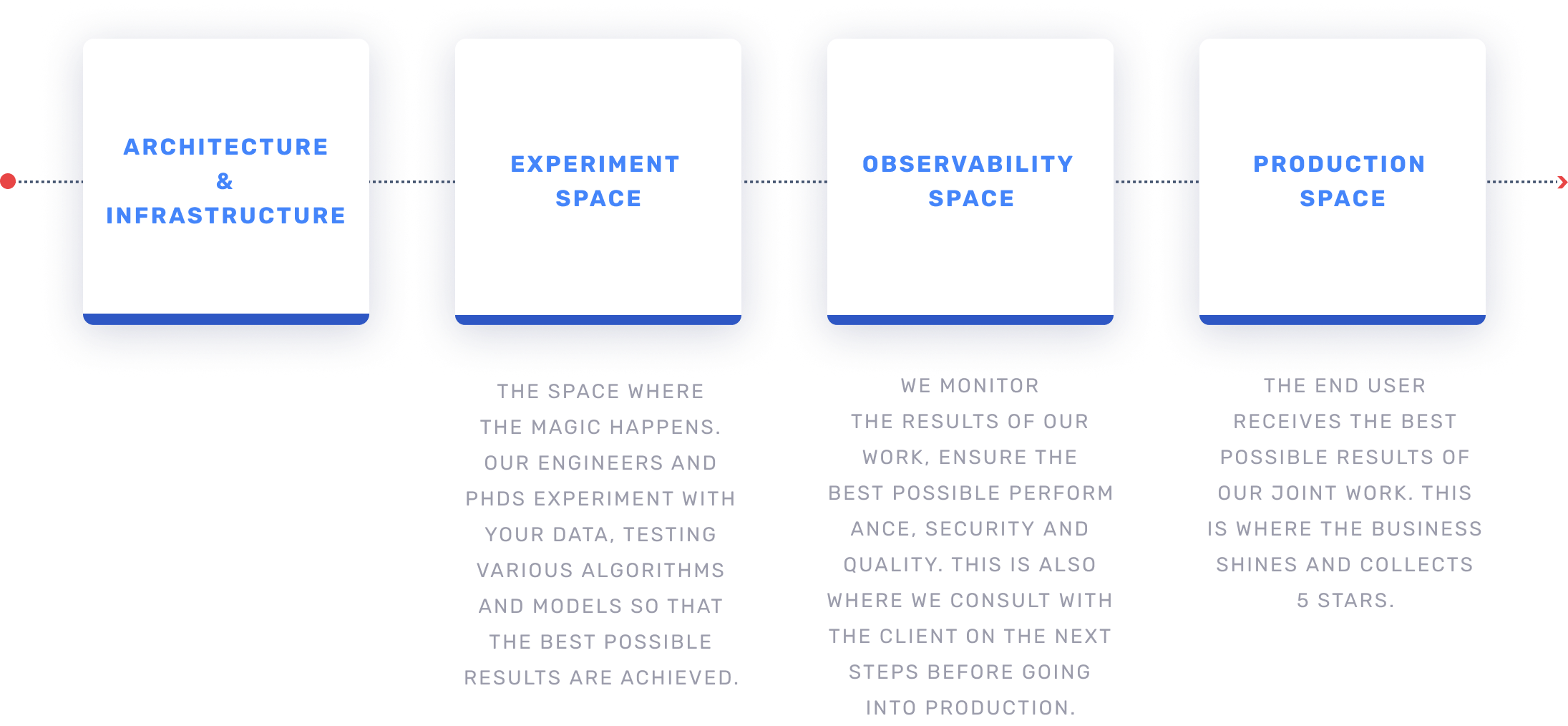

Your Data Journey
Let’s discover how your data travels through AI platforms so that at the end of the day it generates added value for you.
1. Experiment input
Where the journey
begins?
2. Experiment Transformation
Where the magic happens?
3. Experiment output
How the Experiment ends?
4. Production input
When we prepare Production?
5. Production deployment
Where the final touch happens?
6. Go Live & New Experiment
When we Go Live?
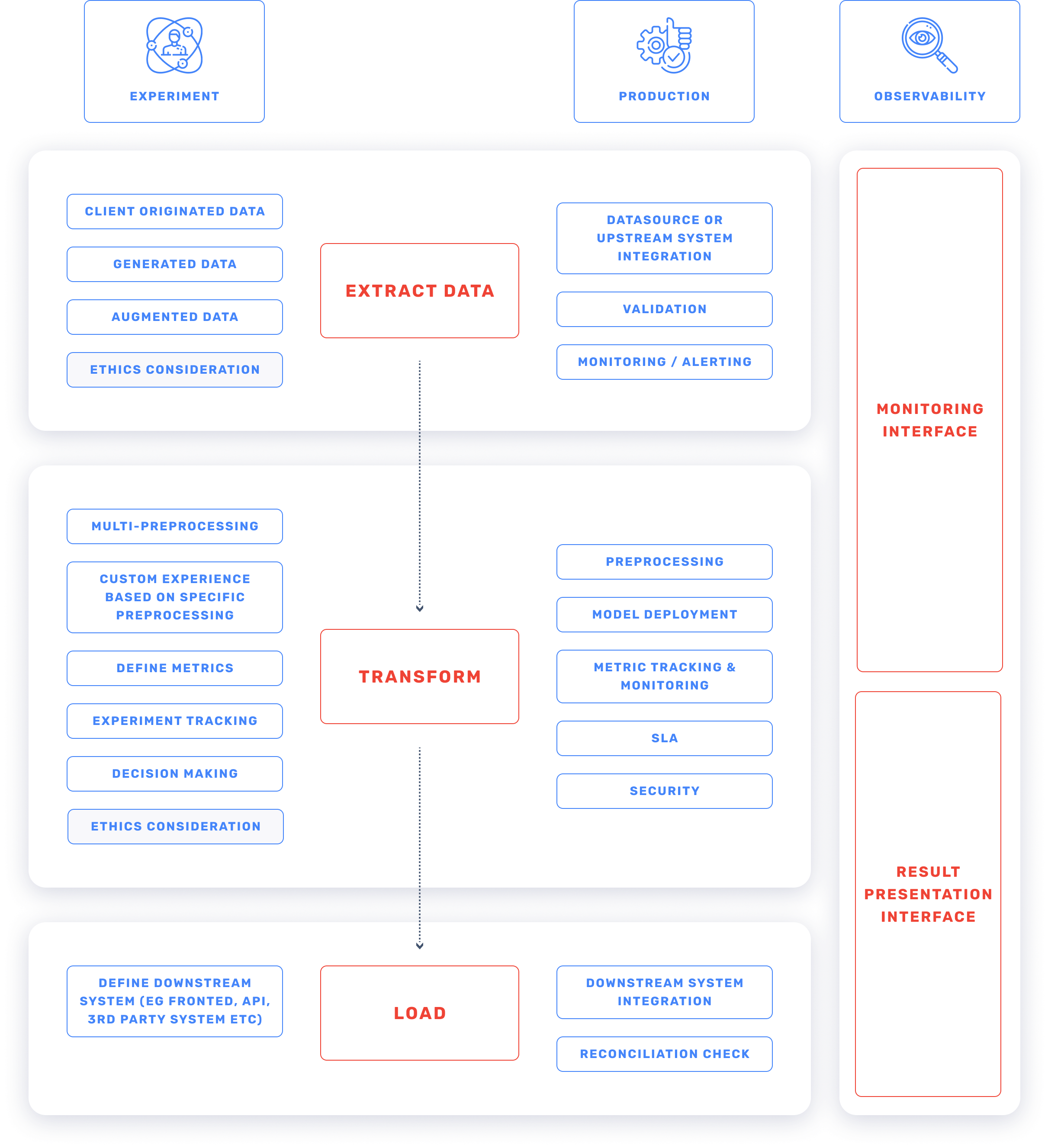
AI projects development framework
Our PhDs and Engineers have prepared a proprietary framework for ML, Data Science and AI projects for our clients. No matter what business problem you come to us with, when it comes to data we will always work according to the following battle-tested methodology.
Download a whitepaper
Let’s find out how to build AI & Machine Learning projects
How do AI Development work?

- Learn how AI, Machine Learning, Deep Learning & Data Science can work together.
- Find out what kind of talents and experts are required for AI Development projects.
- Get to know our unique AI Development Framework, designed by our Ph. D.s and engineers, which includes Experiment, Production, and Observability areas!